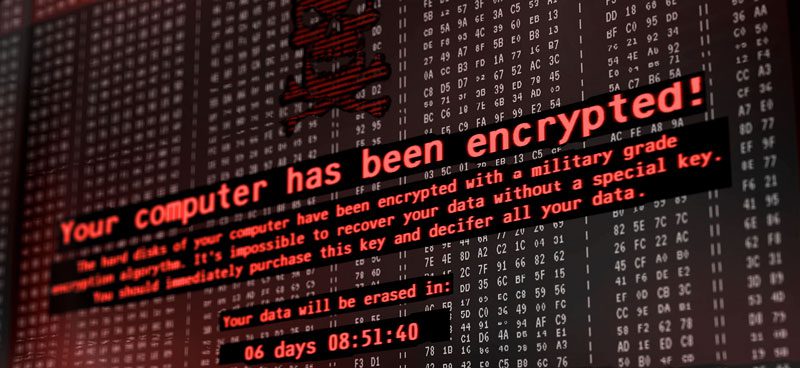
Crypto Ransomware is rampant. Most variants of it (CryptoLocker, TeslaCrypt) are malicious binary files that are very intelligent, aware of their surroundings, and highly polymorphic. Cryptographic ransomware that can morph on the fly makes it extremely difficult for standard signature-based antivirus programs to detect, as well as making it difficult to detect with “Anti-Malware” programs. Intelligent malware requires intelligent endpoint protection to identify, sandbox, and alert before the actual encryption happens to the endpoint.
Cryptographic ransomware is a genre of malicious software that has three goals once it successfully infects a system.
The first goal is to detect if it’s inside of a sandbox or being disassembled. The malware performs checks against the environment like, checking items like hard drive space (usually sandboxes are small), the uptime of the machine, how many programs are installed, etc. If the crypto ransomware feels that the environment is real,
The second goal is to encrypt all of the users’ files using GPG/PGP or sometimes even using their spin on curve25519 or completely unique algorithms written by the author.
The third goal of the ransomware is to perform cryptosporidium or attempt to spread itself across all network shares and machines around it.
Once the crypto malware has infected a machine, it then demands payment to decrypt the encrypted files. This is usually on a time-based system, making every hour more expensive. The attacker requests this payment is usually in bitcoin, but more recent variants have been seen asking for Monero or Ethereum instead, due to the anonymous nature of the crypto coin.
The author of the crypto ransomware will usually target large organizations like hospitals, banks, or cities that cannot afford to lose the data and are willing to pay.
Once criminals gain access to a host, their typical infection chain is to drop the ransomware-birthday package that later installs a second stage cryptocurrency locker system, encrypting the whole system.
Utilizing standard antivirus protection that basis its protection on signatures is not enough to protect against an advanced persistent threat like CryptoLocker, or its variants.
The infection chain begins with remote command execution to download a malicious script that retrieves the code from a known command and control center known only to the attacker.
The issue is not if the target chooses to pay the ransom or not – remember that once an organization has been infected the attackers have already started extracting useful data from the compromised machine and one can now assume that all data on the machine/network has been totally compromised.
This means that network share usernames & passwords personal information, PCI or payment data, internal passwords, customer information, and more has already been exposed and abused, despite paying the ransom.
Generic ransomware is never (or at least rarely) targeted but rather a blast-like attack approach will be performed where attackers acquire lists of emails or compromised websites and blast out ransomware either via e-mail campaign or spearphishing.
A big misunderstanding when it comes to crypto ransomware is not if the target chooses to pay the ransom or not – remember that once an organization has been infected the attackers have already started extracting useful data from the compromised machine(s) and the entire company may now assume that all data on the machine/network/global intranet has been compromised and all information is now in the hands of the attacker.
This includes data on network shares, usernames & passwords, personal information, PCI or payment data, internal passwords, customer information, and all other important documents that the enterprise holds have already been exposed and abused, despite paying the ransom.[/vc_column_text][vc_column_text]
Discover how Volico’s Managed Endpoint Protection Services can protect your business against cryptographic ransomware.
It’s difficult to stop ransomware dead in its tracks, but with Volico endpoint protection real-time binary sandboxing, the malware executes with no impact on the endpoint at all by performing intermediate representation and binary static analysis on the suspect file in real time. This works by executing without relying on signature only based protection by learning about what the intent of the program is and allowing it to run in its own world before ever reaching the target. By utilizing software-focused machine learning and malware intermediate behavioral analysis of static binaries over the wire.
Volico’s Managed Endpoint Protection Services allows the machine to identify malicious files with positive confidence and greatly diminish the number of false positives or legitimate software in the organization by performing inline binary static analysis on the malware, thus interrogating the binary in order to judge it’s intent, malicious activity, or overall trust based on past patterns it performs.
The Volico endpoint protection system will constantly monitor for RFE (rapid file encryption) any attempts of removal of backups and watch for changes to the master boot record. The Volico endpoint security system is also able to stop FAV (file-less attack vectors) even when they are highly obfuscated, deeply entropic, or commanded to start without loading kernel modules, DLL’s or any helpers to further infect the machine.
This is performed by sandboxing the binary and performing binary static analysis and reverse engineering on the suspicious executable to simply watch for its real intent and then track, alert, and inform the primary dashboard about the file’s it’s intent and possible impact.
If the binary is deemed malicious in any way, it’s then vaulted off from the machine and sent to the IRE (intermediate representation engine) for further analysis – all while displaying the information to the enterprise in a dashboard.
Protection is better than cleaning up the mess
Don’t wait until it’s too late and make sure a reliable anti-malware solution protects your business. Volico’s Managed Security Services is your best defense against ransomware and other advanced attacks.
• Call: 888 865 4261
• Chat with a member of our team to discuss which solution best fits your needs.