
How to Avoid Shadow IT Negative Consequences
Shadow IT is the use of IT systems and software that are not approved by the company or organization. Many employees and vendors are using

Shadow IT is the use of IT systems and software that are not approved by the company or organization. Many employees and vendors are using

Blockchain (also called distributed ledger technology) is a new technology form that can be implemented in numerous ways. It is being used because of its

Firewalls are designed to protect your computer infrastructure (networks and computers) from malicious attacks. The firewalls control what information can go in and what data
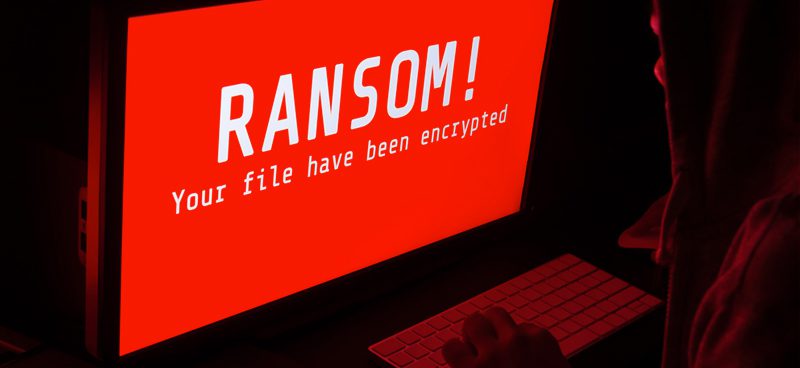
Standard ransomware is the deliberate sabotage of your computer files and data by outsiders. The criminals in no uncertain terms tell you that your information

XaaS stands for ‘anything as a service’ and encompasses SaaS, PaaS, IaaS, and more. As cloud computing has become not simply an option, but practically
Cloud computing is as amorphous a term as a literal cloud, but in reality, there are three basic types of cloud computing. The difference among
It seems axiomatic that physical data security must actually be physically protected. Wouldn’t the best protection come from being physically present to address issues? In
Overcoming the security challenges that small and medium-sized businesses face when accessing the cloud As more and more companies are moving to and working with
Firewalls are a crucial element of web security, but many IT professionals still aren’t clear on the differences between next generation firewalls (NGFW) and web

Ransomware as-a-Service is making cyber crime all too easy. Now, criminals don’t have to create this malicious type of software. They can essentially use it
About cookies on Volico.com
Volico Data Centers use cookies to collect and analyse information on site performance and usage. This site uses essential cookies which are required for functionality. More detail is available in our privacy policy. Learn more