
Discover How Volico Can Protect Your Business Against Microsoft’s RDP BlueKeep Exploit
For the may 2019 security patch release, Microsoft included a patch for a RCE (remote command exec) bug in the remote desktop service (RDP). This

For the may 2019 security patch release, Microsoft included a patch for a RCE (remote command exec) bug in the remote desktop service (RDP). This

Developing a business continuity plan is essential in this age of instant connectivity and will give you the peace of mind that comes with knowing

As business needs grow and evolve, so does the level of the services that they require to operate effectively in a technology-driven world. Due to

The General Data Protection Regulation (GDPR) of the EU and the Health Insurance Portability and Accountability Act (HIPAA) of the United States are two critical

HIPAA is an acronym for Health Insurance Portability and Accountability Act of 1996. It is a U.S. law designed to protect the safety of medical
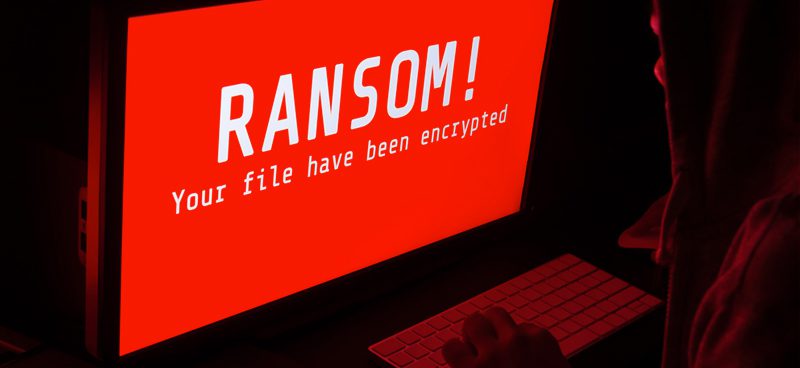
Standard ransomware is the deliberate sabotage of your computer files and data by outsiders. The criminals in no uncertain terms tell you that your information

Ransomware as-a-Service is making cyber crime all too easy. Now, criminals don’t have to create this malicious type of software. They can essentially use it

On Tuesday, February 28th, 2017, an Amazon employee made a typo during a routine billing system repair and, rather than taking only a few servers

Every company should have a storage management plan. As your business prospers, new customers are added, old customers return, new applications are purchased, networks grow

Every company that relies on its information systems for daily operations and for customer relations needs to have a disaster recovery plan in place. The
About cookies on Volico.com
Volico Data Centers use cookies to collect and analyse information on site performance and usage. This site uses essential cookies which are required for functionality. More detail is available in our privacy policy. Learn more