
Transforming Security Strategies: What AI in DDoS Defense Means for the Future
Distributed Denial of Service (DDoS) attacks remain one of the most disruptive threats to IT infrastructure. They flood systems with traffic, degrade performance, and can

Distributed Denial of Service (DDoS) attacks remain one of the most disruptive threats to IT infrastructure. They flood systems with traffic, degrade performance, and can
Vulnerability scanning and penetration testing are methods for assessing the security posture of systems and their resiliency against cybersecurity threats. However, the two are quite
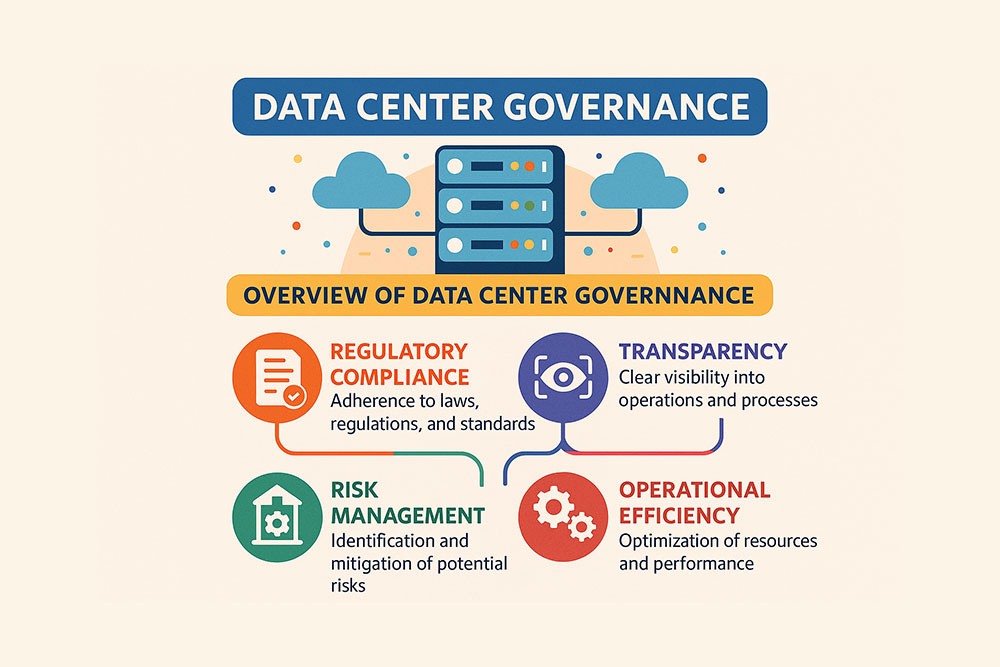
Data center governance is a term that doesn’t ring as many bells as the similar “data governance” does. Nevertheless, its importance, driven by the need

Today’s business landscape is repeatedly disturbed by the devastating fallout of cyberattacks and data breaches. Even well-prepared companies with stringent security measures often find themselves

Organizations today are increasingly relying on multiple different service providers for their many different needs. We have IaaS providers and SaaS providers to cover everything

Data loss prevention (or DLP) is a crucial set of measures for safeguarding an organization’s data from theft or loss. It uses cybersecurity strategies, techniques,

Today, when data availability is becoming as natural as breathing, and our lives are impregnated in almost every aspect with technology, data security is among

Data breaches can cost businesses a lot of money – or, in worst-case scenarios, they can lead to a complete wreck. In 2024, the global

In terms of preventing physical access to equipment, the cabinet is the last potential point of vulnerability in the data center. Because of this, physical

One day, there’s a note on your screen saying that your files have been blocked, and you won’t see them back until you pay a
About cookies on Volico.com
Volico Data Centers use cookies to collect and analyse information on site performance and usage. This site uses essential cookies which are required for functionality. More detail is available in our privacy policy. Learn more